Managed IT Services
End-to-end IT services, tailored to fit your goals, team, and budget
No Long-Term Contracts
We earn your business every month — not just once.
All Omnitech service packages are offered on a flexible, month-to-month basis. We don’t lock you into rigid contracts or bury you in fine print. Instead, we focus on delivering consistent value, responsive support, and results that keep you coming back, because when you succeed, so do we.
No Hidden Fee's
Technology should never come with surprise invoices.
At OmniTech, our agreements clearly define what’s covered, what’s optional, and how projects are billed. If something falls outside your scope, we discuss it with you first. No unexpected charges, no fine-print traps. You get predictable costs, documented deliverables, and full visibility into your IT investment.
Packages
CORE
Base Level Security and Monitoring that Every Business Should Have.-
24x7 Remote Monitoring
-
Microsoft and 3rd Party Patching
-
End-User Security Training
-
DNS & Content Filtering
-
Email Security and Encryption
-
Simulated Phishing Campaigns
-
Enterprise Anti-Virus
-
Endpoint Detection and Response (EDR)
-
Online Computer Backup
SUPPORT
Base Level Security and Monitoring, Plus Unlimited Support-
Everything in Core +
-
Unlimited Helpdesk Support
-
Quarterly Project Hours
SECURE
Advanced Security, Monitoring and Compliance-
Everything in Core +
-
Office 365 (SIEM)
-
Quarterly Project Hours
-
24x7 Security Operations Center (SOC)
-
Email Archiving and Litigation Hold
-
Dark Web Monitoring
-
Duo Two Factor Authentication (2FA)
-
Scheduled Network Compliance Assessment
OMNI
Everything You Need At One Monthly Price-
Everything in Core +
-
Everything in Support +
-
Everything in Secure +
-
Virtual CIO/CTO Services
$2,500 minimum
Custom Pricing Available
We don’t believe in one-size-fits-all IT solutions.
Every business has a unique environment, user count, compliance requirements, security posture, and infrastructure. That’s why all of our service packages are tailored to your exact needs. If the above pricing looks out or reach, give us a call and we can discuss your budget and needs.
After a quick initial consultation, we’ll provide a clear, customized proposal that aligns with your goals and budget — no surprises, no upselling, just what makes sense for your business.
Smarter Protection Through Layers
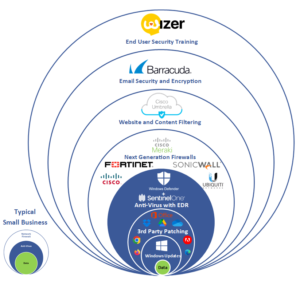
The "Defense In Depth" Approach
Modern threats require more than a single line of defense. That’s why every Omnitech service package is built on a layered security strategy — protecting your business across your people, devices, data, and network. Each layer reinforces the next, creating a resilient IT environment that defends against everything from daily disruptions to advanced cyber threats. It’s proactive, proven, and purpose-built for small businesses. Click HERE for more details.
Let’s Talk About Your IT Goals
Whether you’re just starting to think strategically or you’re buried in tech decisions with no clear plan — we’re here to help.